Virtual Private Networks (VPNs for short) use a technique called ‘Encryption’ to make your transmitted data completely unreadable by any person that intercepts it.
While the math behind encryption is incredibly complicated, actually using and benefiting from encryption is incredibly simple, thanks to the wide availability and compatibility of VPN software.
In this article, you’ll learn about:
- What VPN Encryption is and how it works
- The two types of encryption ciphers (Symmetric, and Asymmetric)
- Encryption strength and the speed/safety tradeoff
- The pros/cons of different encryption ciphers
- The best encryption settings for your VPN software
- How encryption is ‘attacked’ and how to defend yourself
- The NSA, and widespread data harvesting
- Perfect Forward Secrecy (What it is, and why you want a VPN that offers it).
The Basics of VPN Encryption
The goal of encryption is to encode your data so that only your intended recipient is able to decipher (decrypt) the data. Centuries ago, codes were simple because computers didn’t exist. Some codes were even as simple as substituting 1 letter for another (a=z b=x c=f) etc. This map of 1 letter = some other letter is known as a key. It’s the secret information that is required in order to break the code. VPN encryption uses the same concept, but on a much stronger and more complicated scale.
Computers allow us to perform extremely complex mathematical operations in fractions of a second. By using a secret key with trillions upon trillions of different possible values, a VPN can encrypt (encode) your data in such a way that it’s mathematically impossible to decode, without knowing which key you used to encrypt it.
Without the correct key, your data will just appear to be gibberish (known as ciphertext). For example, I used the free message encryption tool at aesencryption.net to encrypt the message:
“The quick brown fox jumped over the lazy dog”
which became the ciphertext…
“7KvDGFhsOp+75keAU0TzcW2vj8VUDeUEBxIrMCL5bMYNmPwsEFQsL2NCVO54rP7L”
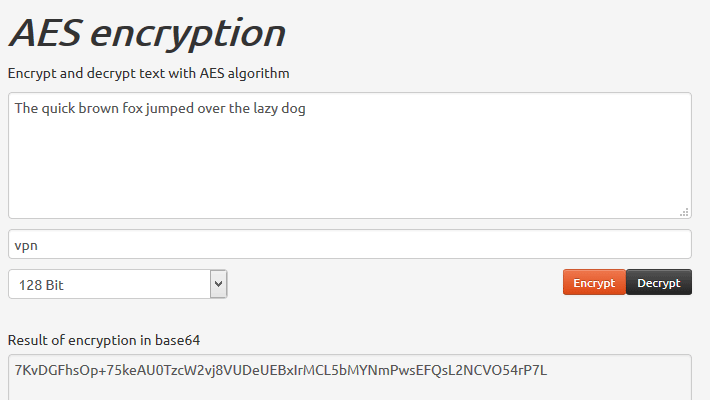
If you change the key (in this case ‘vpn’) by even a single character, the entire ciphertext will change.
Understanding Common Encryption Terms
Let’s look at the most commonly used terms when it comes to VPN encryption. Unfortunately VPN providers use somewhat advanced terminology even in their help documentation, assuming subscribers already know what they mean. Obviously this is not always the case. These overview should give you a better understanding of the most important concepts.
VPN Protocol
The VPN protocol is the framework of data transmission and encryption used by your VPN provider. Most VPNs offer access to several protocols including PPTP, L2TP/IPsec, and OpenVPN.
Some protocols (such as OpenVPN) are extremely flexible and allow multiple options regarding transport, and encryption. For example, OpenVPN supports the full OpenSSL cipher library which allows access to more than 10 unique encryption ciphers (algorithms).
To learn more about VPN protocols, visit our complete VPN protocol guide: PPTP vs. L2TP vs. SSTP vs. OpenVPN which will teach you the pros and cons of each, and when to choose specific protocols. For most users, OpenVPN is the best all-around choice (as long as your device supports it).
Key
The key is like a super-strong password that is known only by you (well your computer anyway) and the VPN server. The key is used to encrypt and decrypt the data you send/receive.
Key Length
Crytographic keys come in different lengths. In general, the rule is: the longer the key, the stronger the encryption. Key lengths are measured in ‘bits’. A bit is a single unit of binary code (which consists only of 1’s and 0’s). Common key lengths include 128-bit or 256-bit.
A 128-bit key consists of 128 binary digits. Since each bit can have two possible values (1 or 0) then a 128-bit key can have 2128 possible combinations (approximately 3.4 x 1038). If a supercomputer could check 1 billion keys per second, it would still take more than 1022 years to check every possible key.
In other words, even a moderate-security encryption strength like AES-128 is EXTREMELY strong.
RSA Handshake
This handshake occurs at the very beginning of an OpenVPN session. RSA is a public-key encryption method that allows you to securely exchange encryption keys with the VPN server each time you launch a connection.
This technique makes it possible to use a new unique key each time you connect to your VPN. Without it, you’d have to keep using the same key over and over (not secure) or get a new key before each session via email or some other method (not practical).
We’ll discuss RSA more when we talk about asymmetric encryption, but basically it’s a technique that uses extremely complex math to allow two people (or computers) to openly exchange secret keys in public, without anyone else being able to actually steal the key.
The minimum recommended key strength for the RSA handshake is 2048-bit. A few VPN providers (such as Private Internet Access) actually offer keys up to 4096-bit strength.
Encryption Cipher/Algorithm
The Cipher or Algorithm is the specific method by which your VPN provider encrypts your data. Each cipher has its own pros and cons. For example, some ciphers have fewer known attacks (weaknesses) but are slower. Others struggle with file sizes over 1 GB.
Some VPN providers will offer a couple different cipher options. The most commonly available OpenVPN ciphers are:
- AES (Advanced Encryption Standard. Orginally known as the Rijndael cipher)
- Blowfish (An older, but fast cipher created by security expert Bruce Schneier)
AES is the most secure option that is widely available. Virtually every VPN provider will offer AES-128 and/or AES-256-bit ciphers.
SHA Hash Authentication
Most VPNs services also include the ability to authenticate messages sent via the VPN. This is done by using a SHA (Secure Hash Algorithm) hash to sign each data packet.
A Hash is a one-way function used to calculate a unique signature for each data packet. A one-way function means it’s very easy to calculate the hash of a message, but virtually impossible to recreate the original message from a hash.
The hashed signature is then transmitted along with the encrypted data. Once you receive and decrypt the data, the VPN will hash it again, and compare the new hash to the hash that was sent with the message. If they match, then the data is authentic.
This protects against ‘Active’ attacks which may attempt to intercept your communications and inject different data. Because the attacker doesn’t have the key to encrypt the injected data, the hashes won’t match.
Another feature of hashing that makes it so useful, is that simply changing 1 character in the input message will dramatically change the resulting hash signature. Compare the examples below, the only difference being a capitalized letter:
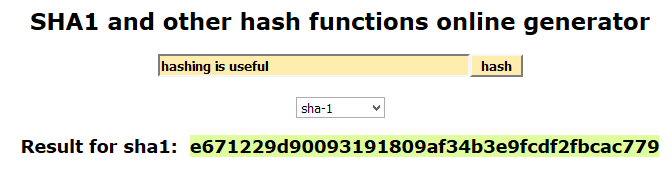
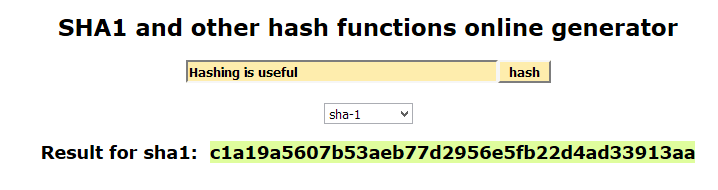
Hash Algorithms
There are 2 main hash algorithms used by VPNs to sign and authenticate your data:
- SHA-1 – this is the fastest authentication method but is now considered moderately vulnerable. One researcher estimated the cost of breaking a single hash at $2.77 Million. It’s unlikely anybody will spend that kind of money to mess with your VPN data, unless you’re a REAL troublemaker.
- SHA-2 – This is the current cryptographic standard, and actually includes a number of different hash algorithms. The most popular of which is SHA-256. This method is more secure than SHA-1 (if you’re extremely cautious) but somewhat slower, so using this algorithm will likely slow your VPN speeds slightly unless you’re on a very fast machine.
Symmetric vs. Asymmetric Encryption
When you use OpenVPN or L2TP/IPsec, you will actually use 2 different types of encryption algorithms: symmetric, and asymmetric. For a quick primer, you can watch this video explaining the each:
Symmetric Encryption
Symmetric encryption means you use the same key to encrypt and decrypt the data. This means that you and the VPN server are using the same shared key. After the VPN connection is established, all data will be encrypted and transmitted via symmetric encryption protocols.
AES and Blowfish are both symmetric algorithms.
The advantage of symmetric encryption is that it’s extremely efficient and fast. This means it doesn’t require much computer processing power to encrypt and decrypt the data. As a result, it’s very useful for transmitting large amounts of data quickly.
Additionally, symmetric encryption requires much shorter key sizes to provide the same amount of security compared to an asymmetric protocol like RSA. Short keys means faster computation, and better speeds.
Typical symmetric key sizes are 128, 192, and 256 bits.
The one weakness of symmetric encryption
Symmetric encryption has one major weakness. You need a way to share the key between the two parties exchanging data securely. One method to share the key would be to use a password, which would serve as the key.
The disadvantage of this method is every VPN session would use the same key (until you changed your password) which means if the key were ever discovered, it would allow an attacker to decrypt the 100% of the data ever encrypted with that key.
The solution?
Securely exchange a new symmetric key for each VPN session. That way, if 1 key is compromised, it doesn’t compromise the data of any past or future sessions. But how can you exchange the key securely over a public network? This is where asymmetric encryption comes in.
Asymmetric Encryption
Asymmetric Encryption is a form of public key cryptography in which each person exchanging data has 2 keys:
- A public key (used to encrypt the data)
- A private key (used to decrypt the data)
VPN services use asymmetric encryption to exchange a new symmetric encryption key at the start of each VPN session.
The way it works is this:
Each person exchanging data has 2 keys. One key is public (everyone can see it) and the other is private (nobody should have this key but you). Your public and private keys will be different from each other, and also different from the public and private keys of the person you’re exchanging data with.
To send a message:
Person A will encrypt the message with person B’s public key.
This public key can only be used to Encrypt the message, once encrypted, it cannot be used to Decrypt the message.
Then person B uses their private key to decrypt the message from person A.
The reason this method works is because the two keys (public and private) are mathematically related in such a way that the private key can be used to decrypt all messages encrypted with the public key. The numbers involved are so large however, and the encryption algorithm is designed in such a way that it is impossible to guess the private key based on the public key.
This type of public exchange is known as a Diffie-Hellman key exchange, and is the basis forward secrecy (which we’ll talk about later on).
Asymmetric Algorithms
The most common asymmetric encryption algorithm is RSA, which is used for OpenVPN’s handshake to exchange the symmetric session keys. RSA commonly used 2048-bit or 4096-bit keys. Because the public key is visible to everyone, the keys have to be much longer in order to be secure.
If you’re wondering how long a 2048-bit key is, here’s the math:
A 2048 bit key has 22048 possible combinations, which is approximately 3.23 x 10616 different combinations.
Why is Asymmetric encryption only used for the VPN handshake
The disadvantage of Asymmetric encryption is it’s not very fast or efficient (because the numbers involved are so large). As a result, it’s generally only used at the start of a session to exchange the (much faster) symmetric encryption keys.
Attacks on VPN Encryption
Worldwide, there are massive decryption efforts being undertaken by governments, spy agencies (such as the NSA) and spy alliances (like the Five Eyes Alliance). The ultimate goal is to be able to harvest and decrypt 100% of encrypted VPN traffic in the world.
Currently, they’re nowhere near this benchmark, but the leaked Snowden documents indicate that the NSA is having decent success with their decryption programs, especially regarding the decryption of PPTP and L2TP/IPsec traffic. So far, OpenVPN appears to be relatively unscathed.
There are two primary categories of attacks:
Active Attacks
Active attacks on encryption are generally man-in-the-middle attacks that involve manipulating or altering the data sent to/from your computer via the VPN tunnel. The goal is to identify patterns based on the manipulated data that make it easier to decrypt the data or guess the secret key.
The best defense against active attacks is hash authentication, which can verify the authenticity of transmitted data packets. Nearly all major VPN providers automatically build authentication into their OpenVPN protocols.
Moreover, active attacks should not be a concern for 99.99% of the VPN-using public. An active attack is a targeted attack against a specific user, service, or computer. It is highly unlikely that visitors to this site are doing anything to generate that level of interest from a spy agency.
Passive Attacks
A passive attack usually occurs after the VPN session has already ended. The NSA stores massive quantities of encrypted data in its servers until such a time that it can be decrypted.
The simplest form of a passive attack is a brute-force attack, which simply tries different key combinations until one succeeds in decrypting the data. As computers get faster, brute force attacks will become more and more efficient (but this can be countered by making VPN keys longer and longer).
The two best defenses against passive attacks are:
- Stronger encryption (longer keys. 256-bit vs 128 bit).
- Perfect Forward Secrecy (use a different key for each session).
What VPN Encryption Settings Should you Use?
We frequently get asked about what algorithm, encryption strength, and authentication mode to use. Hopefully this will clear things up for you.
Rule #1 – Use OpenVPN whenever possible
There is alot of evidence that PPTP and L2TP/IPSec are vulnerable or fully compromised to NSA decryption evidence. On the other hand, there is very little evidence that the NSA has succeeded in breaking AES encryption (the most popular algorithm used with OpenVPN).
Even better, OpenVPN is the protocol built into most proprietary VPN desktop and mobile apps (which is the may the majority of people choose to connect to their VPN service) so there’s a good change you’re using OpenVPN already.
Rule #2 – You probably don’t need 256-bit Encryption (but feel free to use it anyway).
AES-128 is still considered secure, and is regularly used by businesses and governments for secure communications. It’s pretty unlikely that anybody is targeting the decryption of your data specifically, or that the NSA would be terribly interested in what you’re actually doing online.
Since AES-128 is substantially faster than AES-256, most users would be better off choosing 128-bit encryption (if you want to maximize your speed).
If, however, you are generally concerned about keeping your data as safe as possible (for as long as possible) then definitely use 256-bit encryption.
Rule #3 – AES is more secure than Blowfish (as far as we know)
The two most common algorithms offered by major VPN providers are AES (in 128-256 bit flavors), and CBC Blowfish. Blowfish does have some known vulnerabilities, and even it’s creator (Bruce Schneier) recommends using its successors (Twofish or Threefish) but neither algo has seen much adoption among mainstream providers.
The one disadvantage of AES is that it is a NIST standard that was approved (at least in part) with the blessing of the NSA. Does that mean their is a hidden weakness known only to them? Probably not, but it’s possible. The NSA has apparently attempted in the past to deliberately weaken encryption standards.
Additional Thoughts
My basic suggestion is this. If you want to maximize your speeds (while still having solid security) then opt for AES-128. If security is way more important to you than a speed bump, then go for AES-256.
If you’re not sure which algorithm your VPN uses, check their help documentation or just ask support.
You should always leave SHA hash authentication enabled (most VPNs don’t give you the option to disable it anyway). The speed/computational overhead is minimal compared to the security benefits of data authentication.
If you want more control, choose a VPN provider that offers more encryption settings. Private Internet Access is one of the best we’ve found, and gives you control over the encryption strength, handshake, and authentication method.
Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) also known as ‘Forward Secrecy‘ is a method of secure communications, where each session uses a different key, and the decryption or compromise of one session does not increase the vulnerability of any other.
For a VPN to use PFS, two things must be true:
- Each VPN session must use a unique encryption key
- The new key must not be derived from previous keys (but instead be randomly generated).
The key (pun intended) to PFS is the Diffie-Hellman key exchange we discussed earlier in the Asymmetic (Public Key) section of this article. This key exchange method allows you and the VPN server to easily exchange a new session key every time you connect to a VPN server.
PFS is being increasingly used with HTTPS secure web connections as well. Google was one of the first to adopt the standard, but hundreds of websites have now followed suit.
In the past, if a websites encryption key was cracked, all data transmitted to/from that site would be vulnerable. Now, each visit or website session is encrypted with a new, unique key.
How to check for Perfect Forward Secrecy
To see if your favorite bank, credit card, or search website uses perfect forward secrecy, simply click the ‘lock’ icon to the left of the url in your browser bar:
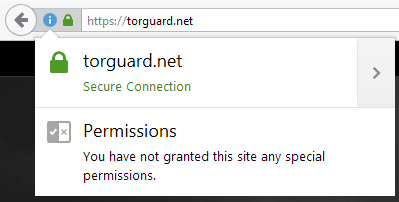
Then click on the arrow in the top right, and if will bring up a window with more information. You’re looking for a line in the technical details that says ‘ECDHE’ which means Elliptical Curve Diffie Hellman Exchange. A DH exchange is required for PFS. For example, here’s Torguard’s:
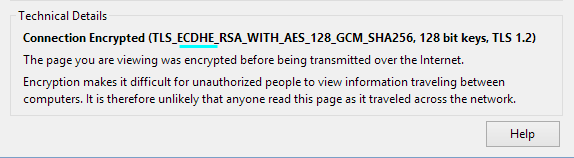
Bank of America, on the other hand, does not (Yikes!).
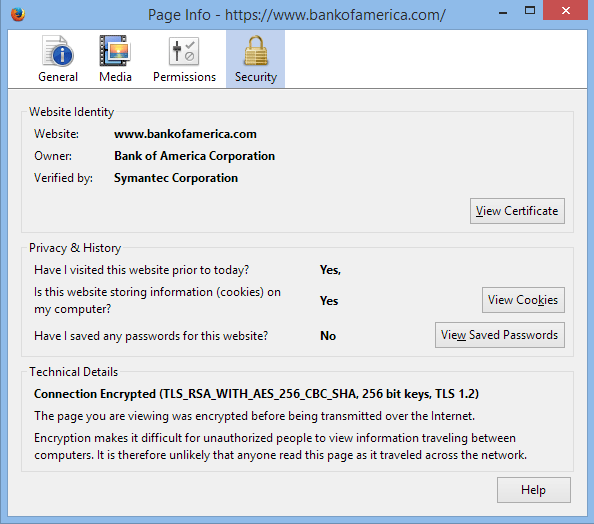
Check the certificates of the websites you use the most. If they don’t use PFS, let them know that you’re concerned. In this day and age, there’s really no excuse for major financial institutions to avoid implementing the most recent encryption standards.
Summary and Final Thoughts
If you’ve read this far, you should now have a decent understanding of how encryption and decryption works, the difference between symmetric and asymmetric encryption, and how they work together to create a secure VPN tunnel.
Just to summarize, here are the main points of this article:
- Encryption is based on mathematical functions that distort data in ways that are very difficult to reverse without having the secret key used to encrypt the data in the first place.
- OpenVPN and IPsec use both Asymmetric and Symmetric encryption to transmit data. The ‘Handshake’ uses asymmetric encryption to share the unique symmetric encryption key for the session. All data for that session is then encrypted with the symmetric key. Symmetric encryption is much faster and more efficient than asymmetric.
- 128-bit AES encryption should be strong enough for most users, and is a good blend of security and speed. If you need absolute maximum security, then choose 256-bit encryption instead.
- SHA hash authentication is used to verify that your incoming/outgoing VPN data has not been altered or tampered with. It prevents ‘Active’ attacks.
- Perfect Forward Secrecy uses a unique symmetric key to encrypt each VPN session. This means that an attacker would have to decrypt each session separately, and decrypting one would not enable them to decrypt any previous or subsequent VPN sessions. Most major VPN services are PFS compatible by default (if you use OpenVPN).
Thanks for reading, and please leave any questions in the comments. We’ll do our best to answer them.



As I understand it, the VPN application on my computer will encrypt my data, on its way to the VPN server. At some point it goes to the web site I am connecting to but what happens to the encrypted data in-between? Obviously someone has the key to decode, decrypt – to unlock the encrypted data.
Obviously as in everything known to man, or woman, there be the unscrupulous amongst us, including perhaps a few VPN providers. What’s to prevent such an animal from ‘sniffing’ my sensitive data or opening the whole can of worms by decoding the data if it had a mind to?
I think I understand how, say a bank using an App on my PC and HTTPS on its server could encrypt and decrypt the data that I send directly to them but how would they be able to decrypt any data I sent encrypted via my VPN? I may be making a mountain of a mole hill but I would like to understand this very basic but critical aspect of VPN usage.
The data is only encrypted between you and the VPN server. This secures it from being inspected by any server in-between you and the VPN. This is usually just your ISP (internet provider). The data transferred between the VPN server and the website you’re visiting is not encrypted (unless the website uses HTTPS like your bank).
You are correct in your assumption that the VPN has full access to your data stream after it decrypts it. This is why it’s incredibly important to choose a trustworthy VPN provider (and why we predominantly recommend VPN companies based in the USA and western Europe). A malicious VPN definitely COULD steal things like passwords or personal data if it is transferred to a non-https website. Though we aren’t currently aware of any specific dangerous VPN providers, it is a good policy to avoid less well-known VPNs as they don’t have a proven track record. And they have very little to lose by betraying customer trust.
If you choose a US-based VPN provider, they would be legally accountable if it turns out they are stealing subscriber data. By contrast, if you sign up with some small VPN in a 3rd-world country and no address, you’ll have almost no recourse in the event of theft/fraud.
The main problem is that privacy is a double edged sword. Companies that offer more privacy (zero logs, no usage restrictions) may also be more difficult to verify or hold accountable.
Pretty soon we’ll have a tutorial in creating your own remote VPN server in about 10 Minutes (easy, low-tech app). It’ll be a bit pricier ($10/15 month server costs) but at least you don’t have to worry about your VPN provider’s integrity.