A 6 letter password can be guessed by a computer in 1 second (if it’s a word from the dictionary). An 9 letter lowercase word (like ‘spaghetti’) takes just under 32 minutes. And when I way guessed, I don’t meant a small chance. I mean 100% certainty that your password can be cracked, using what’s known as a ‘Dictionary Attack’.
This is just one of the many techniques a hacker has at his disposal to gain unauthorized access to your account. And what if you use the same password on multiple accounts? What if the hacker gains access to your primary email account, and from their can reset the password to any of your other accounts!
The damage would be massive, and possibly irreparable.
We’re talking possible loss of money, permanent loss of account access, identity theft, public defamation, exposure of sensitive personal or financial information. Trust me, it would be bad.
Now that I have your attention, let me show you how insecure your passwords really are (and the absolute best practices for protecting the security of online and offline accounts).
In this article, you’ll learn:
- 4 quick tips for stronger passwords (but you’ll learn alot more if you read the whole article)
- How passwords are cracked (an introduction)
- Dictionary Attacks
- Rainbow Tables
- Password Security
- Anatomy of a strong password
- Password Best Practices (unique passwords, 2 factor authentication, etc)
- How to remember/store your strong passwords
- Password Vaults (cloud and self-hosted options)
- Two-Factor Authentication (you need this. Today.)
- Summary and Additional Resources
4 Rules for Strong Passwords
Here are my quick and dirty top tips for maximizing your password and account security in the shortest amount of time. These tips are a good starting point, but if you have the time you’ll learn alot more by reading the entire article.
#1 – Use Strong Passwords
This seems like a no-brainer, but most people don’t know what ‘strong’ means. Here’s a cheatsheat:
- Strong – Use minimum 3 out of 4 (uppercase, lowercase, numbers, symbols)
- Long – 11+ characters minimum. 16 or longer if you ignore rule #1
- Random – It is way easier to break a password containing real words (‘Donkey1975’)
#2 – Use multiple unique passwords
If a site has a data breach and your login/password is stolen (I guarantee this has already happened at least once) how many other sites will the hacker be able to access with your credentials? Ideally you want that that number to be – ZERO.
In reality, most people would have to answer somewhere between “A few” and “Almost all of them…”
Never ever EVER reuse passwords for extremely important websites such as:
- Bank accounts
- 401k/Stock accounts
#3 – Use a Password Vault (to remember your passwords)
The problem with strong passwords is it’s impossible to remember them all. Fortunately, there are multiple ‘Password Vault’ and cloud password solutions that can generate and remember all of your strong passwords for every website. All you need to do is remember 1 single ‘Master Password’.
My personally recommendations:
- Lastpass – Cloud solution, accessible everywhere. Browser extension and mobile support.
- Keepass – Self hosted, encrypted password locker. Stored on your own device.
#4 – Enable 2 factor authentication
Two-factor authentication adds a second layer of security to the login process. A password alone is not enough. You need both the password and access to the authentication device (which is usually your mobile phone which receives verification requests via text or push notifications).
It’s not nearly as much of a hassle as it sounds like, and many 2FA systems only have to verify you once, unless you try to log in later from an unknown device.
The two most important accounts for 2FA:
- Your Password Vault (otherwise if someone steals your master password, they can access any account).
- Your Email (A hacker with access to your email can easily reset passwords to other accounts).
Lastpass has multiple (free) options to add 2 factor authentication to your account. As far as email providers go, most have been slow to adopt 2FA technology. The notable exception is Google, which has had 2 factor authentication on gmail for years.
How Passwords are Cracked
This section will give you a solid introduction into the various ways your password can be compromised (threat vectors). We’ll also discuss the methods used by websites to securely (or sometimes insecurely) store your login credentials.
You’ll also learn how hackers can reverse engineer encrypted password databases (and how to protect yourself).
There are two main ways your password can be cracked:
- Password guessing/brute force attacks
- Reverse engineering passwords stolen from hacked sites.
Password Guessing attacks
These attacks work (both online and offline) by trying multiple different passwords for the same username in rapid succession. A fast computer can try thousands (or even millions) of combinations per second. Guessing attacks work much faster in offline scenarios (cracking an OS or file password).
Guessing attacks against websites will be slower, because the web server will limit how quickly a user can try a new password combination.
Common guessing attacks:
- Brute force – Trying every possible character combination
- Dictionary Attack – Guess the most common words/passwords
Brute Force Attacks
This is the simplest form of password guessing attack. The hacker uses software to try every possible combination of characters in each password length, until the correct one is found.
Since the password requirements of specific websites are publicly known (such as ‘must contain at least 1 number’) the rules of the brute force attack can be tailored to the websites’ minimum password requirements.
There are multiple sites that can estimate the amount of time it would take to crack different passwords with 100% certainty by brute force. You can even see the time differential for a personal PC vs. a botnet or supercomputer.
Sites to estimate your password strength:
Do you think 12 lowercase characters constitutes a strong password? Think again. Here are the brute force results for the password ‘vpnuniversity’ using the Kapersky password tool:
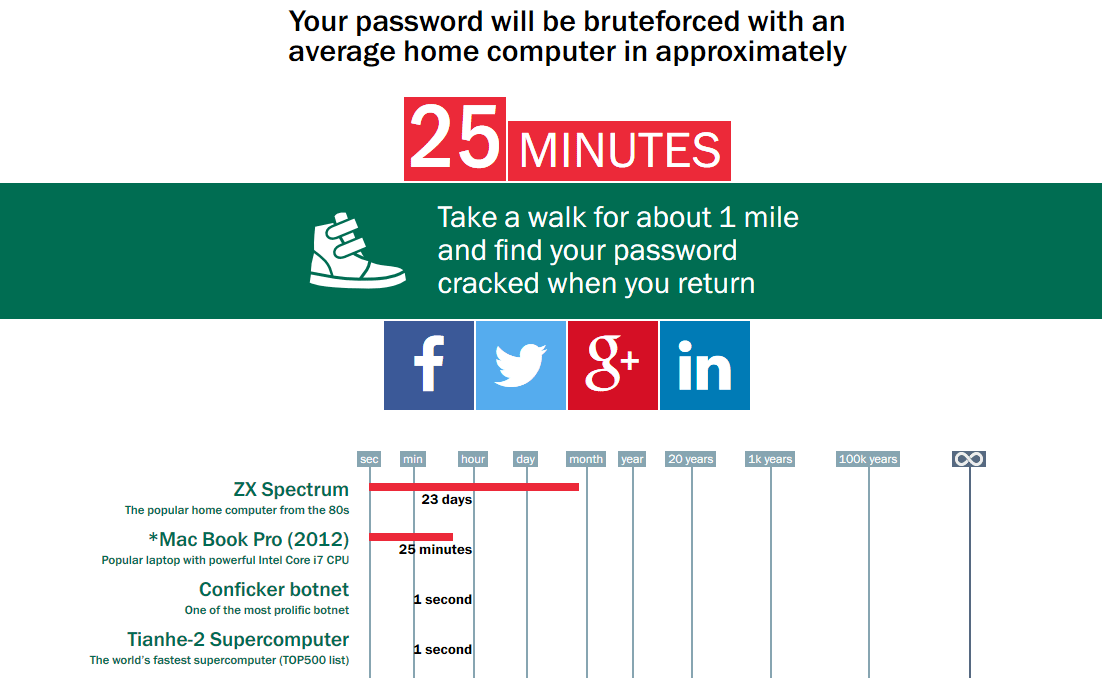
That’s right. A teenage hacker with a 4 year old Macbook can crack a 12 character lowercase password in less time than it takes to watch an episode of ‘Seinfeld’. And a botnet could do it in a single second.
Later in this article (in the password security section) we’ll compare this result to a randomly generated 12 character password containing all 4 character types. Hint: It’s much MUCH stronger.
Dictionary Attack
A Dictionary attack is a brute-forcing shortcut that makes is able to guess passwords much more efficiently by making a specific assumption about your password. Specifically, that your password contains identifiable words and/or common password phrases.
By limiting the password attack to only password combinations including known words (or other common non-word passwords like ‘123123’) an attacker can make a brute-force attack much more efficient. The reason? Only a tiny fraction (less than 0.1%) of all random character combinations will actually contain known words of 4 characters or more.
Advantages: Assuming you use a password that is vulnerable to a dictionary attack, your password could be cracked in less than 1/1000 of the time it would take for a computer to try random character combinations until a match was found. As a result, the vast majority of online guessing attacks are dictionary attacks.
Disadvantages: It is impossible for a dictionary attack to correctly guess a password consisting of purely random characters, numbers and symbols. If the password doesn’t contain a word, a match will never be found, even if the attack runs for an infinite time period.
Data Hacks, Password Encryption & Decryption
While password guessing attacks target only one user at a time, data breaches can expose the login credentials for thousands or even millions of users at a time. There have been multiple MASSIVE data breaches in the past 4 years, including Target, Ashley Madison, and Adobe.
This section will look at the techniques websites do (or don’t) use to securely store your passwords, as well as the most common techniques (like Rainbow Tables) hackers use to reverse engineer encrypted password databases.
How websites store passwords
Most websites that store user data take precautions to store passwords in encrypted form. If properly implimented, even if the user database is stolen during a hack, it will be difficult or impossible decrypt the passwords into plaintext.
Websites store passwords using a technique called ‘Hashing’.
What is Hashing?
At it’s simplest form, a Cryptographic Hash Function or ‘Hash’ algorithm is a set of mathematical rules that transforms any text snippet into a string of random characters of a fixed length (no matter how long the inputted text, the outputted hash will always be the same number of characters).
The mathematics behind hashing is extremely complex, and there are multiple hashing algorithms to choose from, but they all share 1 thing in common, which is at the core of why hashes are a good way to store passwords…
A Cryptographic Hash Function is a one-way function. Which means, it’s easy to compute the hash of a text snippet, but mathematically very difficult (essentially impossible) to mathematically convert a hash back into the original text.
There are also 3 important properties of CHF’s:
- A given text string like ‘password’ will always result in the same hash output
- Changing 1 character of the input (‘passwordy‘) will dramatically change the hash ouput
- It is very unlikely for two different input text strings to generate the same hash output.
There are many free sites where you can calculate hashes yourself to see how the process works. Here are a couple:
- http://www.sha1-online.com – uses the SHA1 hash function.
- MD5 Generator – Uses the MD5 hashing function (no longer considered secure)
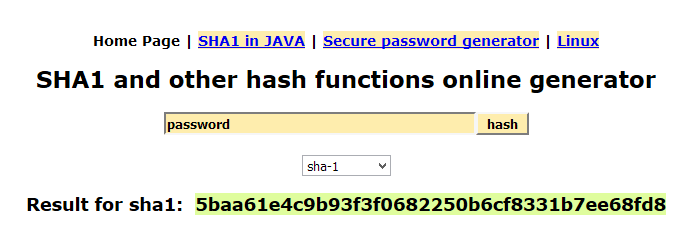
For example, performing the SHA1 hash algorithm on the word ‘password’ results in this:
How websites use hashing for password encryption
When you create a username/password on a combo, the website doesn’t actually store your password in it’s database. Instead, they store the Hash of your password. When you try to log in, the site will calculate the hash of the text you enter in the ‘password’ field, and compare that result to the hash stored in the database. If they match, your login will be successful.
So in reality, the website doesn’t actually know what your password is (which is why you can usually only reset your password, you can’t actually retrieve it if you forget).
The advantage of this is obvious: If the site’s user database is stolen, the hackers won’t actually have your password, they’ll only know the hash of the password, which isn’t sufficient to log into your account.
Wait, why can’t the hacker just login using the hash they stole?
Because when they try to login, the website will calculate the hash of whatever is input in the ‘password’ field. If the hacker just tries to use the hash they stole as the password, the website will actually calculate the hash of the hash which won’t match the login credentials in the database, and their login will be denied.
For example. We already calculated the hash of the word ‘password’ but what if you calculate the hash of the hash? You get this…
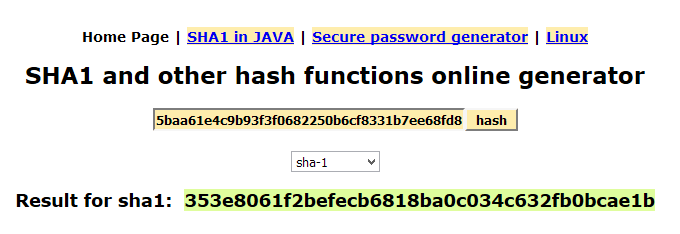
So while they’ve stolen the encrypted hash of your password, they still don’t know what your password actually is. But Mr. Hacker still has a trick up his sleeve. It’s called a Rainbow Table and he might be able to decrypt your password yet…
Rainbow Tables
By definition, a Hash function is mathematically impossible to invert (you can’t calculate the original text based on the outputted hash) so hackers decided to come at the problem from a different direction. The solution? Rainbow tables.
This novel approach is actually more like a brute force method. The hacker wants to decrypt a database of hashed passwords, so he actually uses software to calculate the hash of millions (or even billions) of password combinations. These calculated hashes are stored in a database configuration known as a ‘Rainbow Table’.
Once he has a rainbow table, the hacker can simply compare his database of stolen hashes, to his rainbow table of calculated hashes. Every time the software finds a match, the hacker can easily deduce the password, because the rainbow table maps each plaintext password to it’s hash.
How feasible is a Rainbow Table Attack?
Very, as the Ashley Madison breach proved. Using rainbow tables, the hackers were able to decrypt more than 11 million of the 30 million passwords stolen in the breach, because some of the early users’ accounts were hashed with the insecure algorithm MD5.
Getting access to rainbow tables is surprisingly easy. Believe it or not, you can generate rainbow tables yourself on a home computer using free software like Rainbow Crack. There are also free databases available for purchase, or even for free on torrent sites and hacking forums. There are even free websites that check hashes against tables of precalculated values.
Not surprisingly, hashes of common one-word passwords can be decrypted almost instantly using a free online database (which is much smaller than a real rainbow table).
Were you thinking of making your password your favorite (American) football team? Think again…
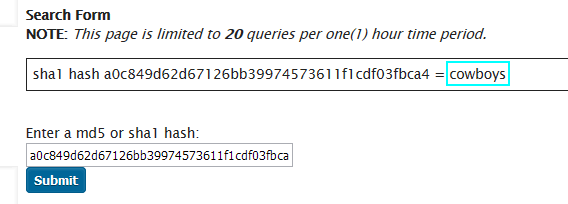
Rainbow Table Weaknesses and Defense
Rainbow tables have one major weakness: there’s a limit to how much data they can store before they become slow, unwieldy or too big to store. A portable rainbow table can only store hashes for all password combinations up to 12 characters in length before it starts to get increasingly unfeasible from a time and cost perspective (that level of processing power isn’t free).
These limits can be stretched a bit if the rainbow table doesn’t include all random character combinations, but instead focuses on known word combinations (like a dictionary attack).
There are two primary techniques to take advantage of this limitation and keep your passwords secure:
- Salting (implemented by the website when hashing your password)
- Stronger passwords (this one’s on you bro.)
Password Salting
Salting is by far the #1 defense against rainbow tables, and proper use of password salting can make the attack almost completely impractical, because it forces the hacker to generate a unique (and large) rainbow table for each individual password they want to crack.
In simple terms, a Salt is a string of random characters that is added to the end of your password before it is hashed for storage in the site’s database. The database stores both the hash, as well as the salt value so that it can correctly calculate the hash each time you log in.
Because each user account users a different salt value when their password is created, any rainbow table created using a known salt (stolen from the database) will only work for reverse-engineering the password of that one user (assuming the salt makes the password+salt length far to long to be stored in a rainbow table).
In order for the same rainbow table to be used to decrypt all hashes in the database, it would have to be larger enough to contain all input combinations the password length + the salt length. By making the salt large enough (even 16 characters would be plenty) calculating the hash of all possible combinations would be beyond infeasible.
Using a different salt value for each user also means that even if two users have the same password, the hash stored in the database will be different for each (because the unique salt is appended to the password before hashing, thus changing the output.
Ashley Madison didn’t properly salt their passwords, which is why it was so easy to decrypt the MD5 hashes stolen in the breach.
Long Passwords
Most companies will follow proper security procedures and use a large salt before hashing your password for storage. By some don’t, either through laziness or ignorance. This is just another reason you should take it upon yourself to make your password as strong as possible.
By making your password 16+ characters, using all 4 character types, you can make a rainbow table attack impractical even against unsalted hashes.
The hackers will be content to reverse the 90% of weak passwords by users that don’t know any better, and your data should hopefully remain safe and secure.
Strong Passwords (Everything you need to know)
If you follow these recommended best practices for password selection and storage, you will dramatically reduce you risk exposure in the event of a data breach. Nobody can guarantee absolute security (certainly I can’t) but these principles are a massive step in the right direction.
What constitutes a strong password?
A good password should ideally be as long as possible, as random (or at least seemingly random) as possible, and contain as many character types as possible:
The 4 character types are:
- uppercase letters
- lowercase letters
- numbers
- symbols
To illustrate how important it is to add as many of these 4 character types as possible when you create a password, let’s consider the difficulty of breaking your password via brute force:
There are 26 lowercase letters (in the English alphabet) so an 8 character all-lowercase password has 268 unique combinations.
If you add uppercase letters, numbers 0-9, and 10 symbols (the 10 available by pressing SHIFT + [a number 0-9]) you get 72 unique character choices. In an 8 character password, this yields 728 unique combinations.
Do you want to guess how many more possible combinations there are when you use 72 characters for your password?
Let’s do the math:
268 = 208,827,064,576
728 = 722,204,136,308,736
728 / 268 = 3458 (rounded to the nearest integer).
In other words, if it took 1 day to crack the first password, it would take almost 10 years to crack the second.
When you go to 12 characters, the difference is even more dramatic:
7212 / 2612 = 203,381 times as strong.
The rules for a good password:
- Strong (multiple character types)
- Long (11 character minimum, 13+ is better)
- Random (Avoid using common words vulnerable to dictionary attacks).
Password Best Practices (Will minimize your exposure after a data breach).
Follow these simple rules to minimize the damage (if any) that could result if hackers stole a database containing one of your passwords.
Rule #1 – Use Unique Passwords (Especially for important accounts).
Most people use the same password over and over for different accounts. The problem with this is obvious. If a hacker steals your password, he now can access any account that uses that login/password combination.
If you use a unique password for every account, the theft of one password doesn’t make any of your other accounts vulnerable. Password vaults like Lastpass have a built in random password generator then can help you pick a unique strong password for every site.
There’s no reason someone should be able to access your bank account just because they hacked your twitter account (and if you believe celebrities, Twitter gets hacked all the time). Use unique passwords.
Rule #2 – Enable 2-factor authentication for your important accounts
If you aren’t using 2FA yet, you should be. It very difficult for someone else to take control of your account, even if they have the correct login/password combination. It’s easy to implement, available on many sites, and usually free.
What is Two-Factor Authentication
2FA (sometimes also called two-factor verification) is a security measure that requires users to complete 2 separate steps before accessing an account. The most common 2FA combination is:
- Something you know (login/password combination)
- Something you have (Smartphone, security token, flash drive, etc…)
After you type in your login/password, you use the your physical verification device to complete the login. Often this will be in the form of a text message or push notification being sent to your smartphone, which contains a unique (and temporary) verification code.
Even if a hacker does manage to decrypt your password, it’s highly unlikely that he’ll be able to get his hands on your authentication device (unless he’s really motivated).
Where to use 2FA?
While many websites do offer 2-factor authentication, the majority don’t. It also adds a small amount of time to the login process, so it’s usually only worthwhile for the most important websites.
There are 3 main categories of sites for which we STRONGLY recommend enabling 2FA:
- Your primary email account
- Your password cloud vault (if you use one)
- Bank/Brokerage accounts
Why these account types?
Bank/Brokerage/Retirement accounts – These accounts are obvious choices for 2FA, because an account breach would be devastating. The bulk of your net worth (outside your house if you own one) is basically just digits in a computer database. If a hacker gained access to your account, he could transfer your life savings to another account, and you’d be, as we say, Shit Outta Luck.
Email/Password vault accounts – In many ways, these accounts are actually the most important, because their gateway accounts. If a hacker can access your email, he can reset your passwords for any website that uses that email address. A password vault is even more dangerous, and if compromised, the hacker could literally download all your login combinations is plain text. Yikes.
There’s a bit of bad news, however. Very few Email providers have deemed 2FA worth the effort. Fortunately, google continues to be on the cutting edge of personal security. Enabling 2-factor authentication for Gmail is quick and easy.
Why you need a password manager
The trouble with strong, unique passwords is that they’re impossible to remember. Literally.
That’s why millions (possibly billions) of users have turned to password management services like Lastpass, Keepass, Dashlane, and 1Password. All you need to remember is 1 single ‘Master Password’ and the password manager does all the heavy lifting and storage of your online credentials.
Most of these services are ‘cloud-based’, meaning your password vault is available from any location with an internet connection. Your passwords will be stored in an encrypted database, using the same technology as professional hard drive encryption (which should still protect your data even if the database is hacked).
There are two types of password managers:
- Self-hosted (offline) solutions.
- Cloud (online) solutions
Both cloud and self-hosted password managers accomplish the same thing (storing and remembering all your passwords in encrypted form) but each has it’s own pros and cons.
Self Hosted vs. Cloud-based password managers
The majority of password management services are now cloud-based because the cloud allows users to sync their password across all devices and access their passwords from any device with an internet connection. While this convenience is a huge benefit, there are also two caveats:
- You have to trust your password management company not to lose (or even steal) your passwords.
- You have to trust their ability to encrypt and protect your passwords from theft by others.
Bottom Line: As long as you’re sticking to the most trusted names password management, your data should be secure and you can trust that your passwords are being protected using industry-standard best practices like:
- Zero-knowledge encryption (Only you have the encryption key)
- HTTPS encrypted data transfer of passwords to/from your vault
- Salting of hashed passwords (so they’re difficult to reverse engineer even if your vault is breached).
Our 3 favorite password managers
Our 3 favorite password managers (not in order) are:
Each has it’s own advantages, and which one you should choose will depend on your budget, privacy preferences, and whether you prioritize convenience more than security.
Lasspass (Cloud | Freemium)
Lasspass is a cloud-only password manager that makes your login details easily accessible from any device.
They operate on a freemium pricing model, where the PC browser extensions or free but you have to pay to access your lastpass vault from your mobile device.
How Lastpass Works
You use Lastpass by installing their extension for your favorite web browser (all major browsers are supported). You sign into your lastpass account with a single ‘Master Password’ which then gives you access to your full Lastpass ‘vault’.
Lastpass will automatically pre-populate login/password fields for saved sites (or even autologin if you prefer).
All your usernames/passwords are encrypted locally before sending them to the lastpass cloud using AES 256-bit encryption. Lastpass doesn’t even know your Master Password (they just store a salted hash of it for login verification). It’s a true zero-knowledge password manger.
Is LastPass secure?
Very. Your entire database is stored in encrypted form, so even if data is stolen from their cloud servers, it’s extremely unlikely hackers could break the encryption protecting your passwords.
Lastpass was actually hacked in 2015 but the intruders weren’t able to compromise user accounts thanks to the multiple redundant security measures Lastpass implements.
Two-Factor Authentication
Make your Lastpass vault even more secure by enabling 2-factor authentication (they offer multiple options, many of which are free). This makes it nearly impossible for a hacker to access your account, even if they have your master password.
Pricing
Lastpass is a ‘Freemium’ service. Basically it’s totally free to use the lastpass in your favorite web browser but you have to upgrade to sync passwords to your smartphone or other mobile device. Premium is only $12 annually.
Dashlane (Local + Cloud Sync | Freemium)
Dashlane is another Freemium password manager like Lastpass. They have even more features but the free version only works on a single device. To get the most out of Dashlane, you’ll need to upgrade to their premium plan which costs $39.99/year.

How Dashlane Works
At it’s core, Dashlane is very similar to Lastpass. Your password database is encrypted locally using a master password that only you know. You can easily access your passwords with the Dashlane browser extension (all major browsers) or the Dashlane app on your smartphone/tablet.
Features
- 256-bit AES Encryption (Zero-Knowledge)
- Securely sync your passwords to the cloud
- Access your passwords from any device
- Change all your passwords in 1 click (over 250 sites supported).
- ‘Strong’ password generator
- Securely store your credit card information
- two-factor authentication (optional)
By far the most unique features is the 1-click password change, which can instantly change all of your passwords at over 250 of the world’s most popular websites like Evernote, Amazon, Spotify and more…
Pricing
Dashlane is free on any 1 device or you can upgrade for $39.99/year to support multiple devices.
Keepass (Local Database w/ sync option | Free)
Keepass is a completely free password manager that stores your logins/passwords in an encrypted database on your own device. There are third-party projects that add support for mobile devices as well.
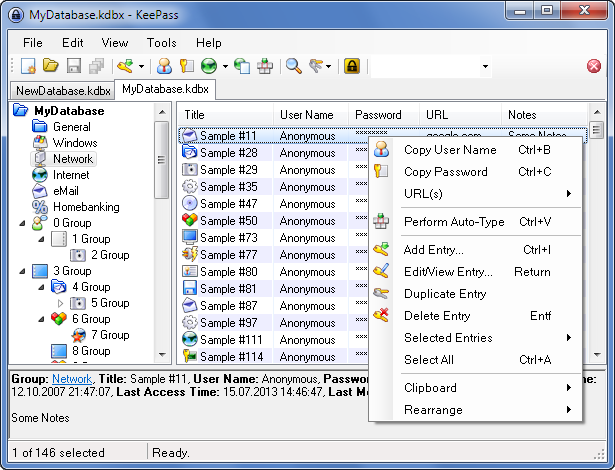
How it works
Usernames/Passwords are all stored in a local database (on your own machine) which can be encrypted with your choice of cipher algorithm including: AES, Blowfish, or Twofish.
The database is encrypted using a ‘master password’ with the option to add a ‘key file’ if you prefer. Keyfiles are a form of two-factor verification which allows you to use any file on your computer as a secondary ‘key’ required in addition to the password.
You can drag and drop login/passwords from keepass to your web browser, or use one of the many free extensions to auto-fill password fields directly from keepass.
Mobile Support
Keepass was originally developed only for Mac and Windows machines, but it has also been ported to iOS and Android by 3rd-party developers. You can use one of the following apps to sync your Keepass vault to your mobile device:
- KeepassDroid (Android)
- Keepass2Android (Android)
- MiniKeePass (iOS)
Wrapup
Now that you know why your 6-9 character lowercase passwords are so unsafe, make sure to take the steps to do something about it. The only person looking out for you online security is you.
It’s inevitable that hackers will steal a database containing your login/details (in all likelihood, it’s already happened whether you realize it or not).
By using strong, unique passwords you can minimize the chance of a hacker reverse-engineering your password (assuming the site followed proper ‘hashing’ practices). And by never using the same password twice, you don’t have to worry about a stolen password being used to log into multiple sites.
Store all your strong passwords in a password manager (like lastpass) and upgrade your security with 2-factor authentication.
Hackers mostly go after the low-hanging fruit (meaning people with short, easy passwords). By following these simple rules, you’ll make yourself a much less attractive target. Get to it.