Perfect Forward Secrecy (or just ‘Forward Secrecy’) is a valuable privacy feature that can make your VPN sessions much more secure, and help prevent the decryption of your web history.
Wikipedia defines Forward Secrecy as:
“…a property of secure communication protocols in which compromise of long-term keys does not compromise past session keys.”
What that means in simple terms is this:
Think of VPN encryption like a lock/key combination. With perfect forward secrecy, each VPN session uses a different lock/key combo, so even if someone steals (or guesses) one key, they won’t be able to unlock (decrypt) any other VPN sessions.
Perfect Forward Secrecy (PFS) is a massive leap in privacy technology, and VPN’s that implement it will be much more effective at keeping your internet activity safe, and secure.
In this article, we’ll explain Forward Secrecy in detail, as well as show you which VPN providers/protocols offer it.
The Best VPNs with Perfect Forward Secrecy
This is a short list of recommended VPN providers that implement PFS on their VPN network. This list does not include every VPN provider with forward secrecy.
As you’ll learn later on, OpenVPN (when properly configured) enables PFS right out of the box. So any provider using OpenVPN is at least capable of forward secrecy.
| Rank | VPN Provider (review) | Logging Policy | Best Price | Website |
|---|---|---|---|---|
1 | Private Internet Access | zero logs | $3.33/m | Visit |
2 | VPN.ac | 1 day connection logs | $4.83/m | Visit |
3 | IPVanish | connection logs | $4.80/m | Visit |
4 | Proxy.sh | zero logs | $3.33/m | Visit |
5 | ExpressVPN | connection logs | $8.32/m | Visit |
What is Perfect Forward Secrecy?
To have perfect forward secrecy (for a VPN) each VPN session must use a unique key (used to encrypt your transmissions) that is not derived from any previous session or key.
The advantage of this is simple: even if an attacker somehow steals or guesses the key to 1 encrypted session, they won’t be able to decrypt any past or future VPN sessions, because that key will only ever be used once (by you).
Some VPN providers even change the encryption key mid-session. For example, Private Internet Access rotates the key every 60 minutes, which ensures your security even during long VPN sessions (think days or weeks).
Perfect Forward Secrecy Requirements
In order for your VPN communications to have PFS, the following must be true:
- Each VPN session uses a new, unique encryption key
- New keys are not derived from previous sessions
The Benefits of using PFS
Imagine you were staying in a hotel but you lost your room key. The front desk makes you a new key, but doesn’t actually change the keycode on the card.
Now imagine that every time you stay in a hotel room for the rest of your life, your room key uses the same key code. Whoever found they key you dropped would have unlimited access to any hotel room you stay in, for life. Not very safe is it?
That’s how a VPN works without perfect forward secrecy. If someone managed to steal, guess, or find your encryption key, they’d have unlimited access to anything transmission encrypted using that key.
With perfect forward secrecy, each session key is unique, so an old key cannot decrypt your new communications. At the end of a VPN session, you could broadcast your encryption key on twitter and it wouldn’t harm your future security at all.
How Perfect Forward Secrecy works
Unlike weaker encryption protocols that rely on the same encryption key over and over (like those derived from a password), Perfect Forward Secrecy requires the VPN server to generate a new encryption key at the start of each session.
It’s also critical that this key be exchanged securely (so a man-in-the-middle can’t steal the key and decrypt your traffic).
The method for this secure exchange is called a Diffie-Hellman key exchange (invented in 1976), and named for it’s creators (who just won the Turing prize for computing in 2015).
Even though it was invented 40 years ago, the Diffie-Hellman exchange (and newer variants of the same principle) are still being used to ensure privacy and security for encrypted connections today.
The best description of how a Diffie-Hellman exchange works in principle can be found in this Khan academy video:
The two stages of a VPN connection
There are two phases of any VPN connection (when using PFS). The handshake, and the tunneling phase.
The Handshake
The handshake happens at the very beginning of a session, and this is where they Diffie-Hellman exchange happens. The purpose is to authenticate both the server (the VPN provider) and the client (you) and then securely exchange an encryption key that will be used to encrypt all data during the VPN sessions.
Whether or not your connection has PFS depends completely on the way the handshake is configured.
The Tunnel
The tunneling phase is the primary phase of the VPN connection. Once the encryption key is exchanged between you and the VPN server (during the handshake) you can now use it to encrypt, transmit, and decrypt data send through the VPN tunnel.
Which VPN Protocols have Perfect Forward Secrecy?
While several VPN protocols are PFS capable, actually implementing forward secrecy requires specific configuration rules by your VPN provider. So just because L2TP/IPsec can use PFS, doesn’t mean it’s configured to do so.
The two VPN protocols most commonly used with PFS are: OpenVPN and L2TP/IPsec.
OpenVPN
OpenVPN is an incredibly strong and flexible VPN protocol, and is the workhorse behind most consumer-grade VPN software out there. It is fully PFS capable out of the box, and the vast majority of VPNs offering OpenVPN connections will use forward secrecy by default.
L2TP/IPsec
While L2TP doesn’t always use PFS, it is PFS capable thanks to IKE and IKEv2 (Internet Key Exchange) which enables a Diffie-Hellman style exchange during the VPN handshake.
VPN Providers that offer Perfect Forward Secrecy
These are some of our favorite VPN providers who are fully PFS-compatible (with OpenVPN and L2TP/IPSec). They are not the only choices, but they are all well-known companies with strong networks and feature-rich software.
When it comes to choosing a VPN, trustworthiness and reputation are 2 of the most critical factors.
Private Internet Access
Private Internet Access (affectionately known as PIA) is a true non-logging VPN provider based in the USA. They’re widely considered one of the most torrent-friendly and privacy-friendly VPN providers in the world. It should be no surprise that their software uses Perfect Forward Secrecy by default.
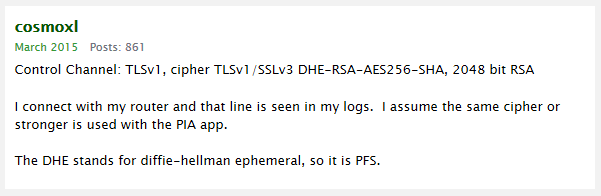
Forward Secrecy with PIA
There have been multiple discussions in PIA’s forums, regarding clarification of whether they are a PFS-enabled VPN. As subscribers’ VPN troubleshooting logs show in the screenshots below, PIA runs OpenVPN mode and uses a Diffie-Hellman exchange (abbreviated DHE) which is the basis of PFS.
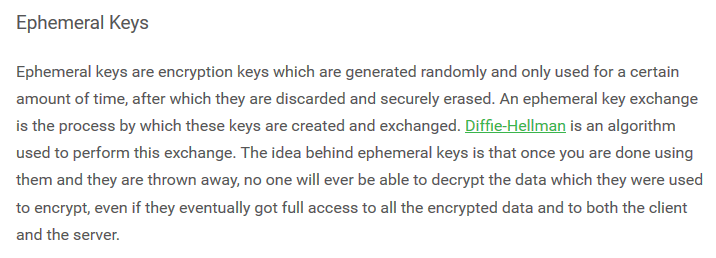
and of course, there’s PIA’s own discussion of their use of ‘Ephemeral Keys’ on their encryption help page:
Other Features:
Beyond PFS, PIA offers several notable privacy & security features. Among them:
- Their legendary ‘Zero-Logs Policy’
- Adjustable encryption strength and choice of ciphers
- SOCKS5 proxy included
- Unlimited speeds/bandwidth
- Pricing starts at $3.33/month.
Read our Private Internet Access Review for full features, specs, and security analysis. Or just get to the fun part and…
VPN.AC
VPN.ac is a security-first VPN provider based in Romania. Their team is constantly innovating new security features, including using zero-log private DNS servers (obfuscated with millions of random DNS queries), a secure proxy extension for chrome and Firefox, and of course…perfect forward secrecy.
Perfect Forward Secrecy with VPN.ac
VPN.ac prominently advertises their Forward Secrecy capabilities right on their ‘Features’ page. They also advertise their extremely strong encryption and cipher suite, which beats the industry standard:
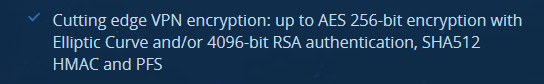
And of course I was able to verify that OpenVPN was using a Diffie-Hellman key exchange by looking at the connection logs in my VPN software:
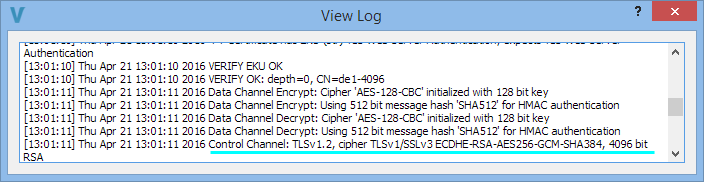
Other Features
VPN.ac prides itself on offering better and stronger security than their competitors. Their impressive features list includes:
- Custom Encryption Control – choose your preferred encryption strength & cipher. You can even use cutting-edge DHE algorithms like ECC (Elliptic Curve Cryptography).
- Encrypted zero-log DNS servers – Don’t worry about your ISP (or even the NSA) snooping on your web history. All DNS lookups with vpn.ac are encrypted, non-logged, and obfuscated with millions of randomly generated DNS requests.
- P2p/Torrent Optimized servers – VPN.ac allows bittorrent and filesharing in all server locations, but they recommend you use their P2P-optimized servers which have massive bandwidth, better p2p packet routing, and are located in filesharing-friendly countries.
All plans include unlimited speeds/bandwidth, and a 7-day refund policy. Pricing starts as low as $4.83/month.
Try VPN.ac Risk-Free for 7 Days
Non-VPN uses for Perfect Forward Secrecy
There’s another form of encrypted web traffic even more prevalent than VPN usage: HTTPS/SSL web traffic.
We’ve discussed https using PFS in an earlier article, but let’s take another crack at it.
But let me make one thing clear before we start…
HTTPS can be implemented with Perfect Forward Secrecy, but unfortunately it usually isn’t. The good news is that trend is starting to change.
We’ll look at the benefits of using PFS and HTTPS together, but we should probably start at the beginning…
What is HTTPS?
You probably already know that websites use the HTTP protocol. That’s why every web address starts ‘http://www…”.
HTTPS is simply the encrypted form of the http protocol.
HTTPS is what makes online shopping possible. Without it, anybody snooping on a websites traffic could steal whatever private information you transfer to/from the site, such as:
- login/passwords
- Social Security Numbers
- Credit card information
In technical terms, HTTPS is the HTTP protocol, encrypted with either SSL (old) or it’s successor TLS. That’s right…TLS, the same encryption library used with OpenVPN that makes Perfect Forward Secrecy possible.
Who uses HTTPS?
You can identify when a website is using https by the ‘Lock’ icon in your browser bar, as well as an ‘https://’ at the start of the web address in your browser’s URL bar. Here are some examples:
Every major online retailer uses https in the shopping cart (to secure your payment info) and often on the entire website.
Google uses full-time https to encrypt your search results and protect your privacy.
Your bank, credit card company, and online broker all use https to keep your sensitive financial information secure.
Why should HTTPS use Perfect Forward Secrecy?
When you stop to think about it, PFS is probably even more important for online commerce than the casual VPN users. Without PFS, an https website just uses the same private encryption key over and over. Over time, this would make it easier and easier for an observer monitoring the websites traffic to guess the private key the website is using for the handshake.
If the attacker does successfully discover the key, he will be able to decrypt all past, present, and future transactions encrypted with that key. On a popular e-commerce site, this allow someone to steal thousands, even millions of credit card numbers.
How to check if a website uses Perfect Forward Secrecy
Every website using https encryption has a public ‘Security Certificate‘ that can easily checked while browsing that site to determine what type of encryption the connection is using.
In Chrome, it only takes two clicks.
- Click on the ‘lock’ icon to the left of ‘https://…” in your browser bar
- Click the ‘Connection’ tab in the window that pops up
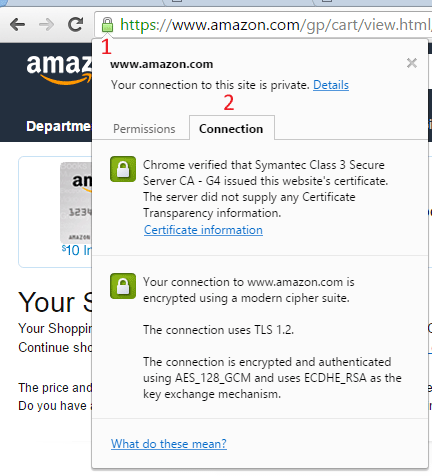
As we already learned, a Diffie-Hellman Exchange (DHE) is the critical ingredient that makes PFS possible. Looking at the image above, do you think Amazon has Perfect Forward Secrecy enabled?
As a matter of fact, they do:
‘ECDHE_RSA as the key exchange mechanism’ means that amazon uses an elliptic curve Diffie-Hellman exchange to send the 128-bit AES encryption key to your web browser. Diffie-Hellman = Perfect Forward Secrecy.
Unfortunately all is not rosy in the land of PFS. Amazon is the exception rather than the rule, and the vast majority of online retailers and financial institutions do not use Perfect Forward Secrecy!
As we can see from JP Morgan Chase’s certificate on chase.com…
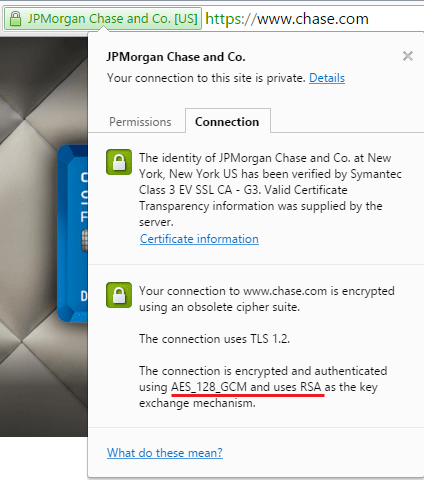
Chase doesn’t use a Diffie-Hellman exchange, and instead opt to use the same private key to encrypt session after session. As computing power gets faster and encryption cracking more efficient, this could potentially leave their customers vulnerable if they don’t upgrade to a Diffie-Hellman exchange.
Perfect Forward Secrecy and NSA Surveillance
Consider PFS and it’s implications regarding protection from NSA surveillance. With a company like Chase who doesn’t use perfect forward secrecy, the NSA needs only ask for, guess, or steal Chase’s private encryption key.
Once they have it, they could decrypt all past and future encrypted communications from that website (we already know the NSA is storing encrypted traffic indefinitely).
With Perfect Forward Secrecy enabled, the NSA would be forced to decrypt every single session separately, and discover the unique private key for each (an infinitely harder task). It almost makes you wonder why major financial institutions have been so slow to adopt Diffie-Hellman style PFS key exchanges…
More on this theory, and a solid explanation of encrypted key exchanges in this video (it’s long, so skip ahead to 1:15:39).
The discussion on SSL, PFS, and the NSA starts at 1 hour and 15 minutes in.
Summary
If you’ve made it this far, you should have a solid understanding of Perfect Forward Secrecy. You learned how it works, how to recognize if a VPN or website is using it, and which VPNs offer it.
The benefits of PFS cannot be overstated. It is a massive leap forward in security technology.
In simple terms:
Perfect Forward Secrecy protects the integrity and security of all other past and future encrypted connections, even in the event that an attacker learns the key to a past or present session.
Because: PFS allows each connection to be encrypted with a new, unique key that will (almost certainly*) never be used again by you.
* There are 3.4 x 1038 possible unique 128-bit AES encryption keys. So it’s highly improbable that you’ll ever use the same key twice, but not impossible.
VPNs using Perfect Forward Secrecy
Most VPNs using the OpenVPN protocol will have PFS enabled. Below are 5 of our favorite VPNs that definitely offer PFS…
| Rank | VPN Provider (review) | Logging Policy | Best Price | Website |
|---|---|---|---|---|
1 | Private Internet Access | zero logs | $3.33/m | Visit |
2 | VPN.ac | 1 day connection logs | $4.83/m | Visit |
3 | IPVanish | connection logs | $4.80/m | Visit |
4 | Proxy.sh | zero logs | $3.33/m | Visit |
5 | ExpressVPN | connection logs | $8.32/m | Visit |
Additional articles and resources:
If you want to learn more about Perfect Forward Secrecy, how it works, and how it’s implemented; you’ll enjoy these articles.
- An Introduction to Perfect Forward Secrecy
- PFS can stop NSA spying out websites (but nobody uses it)
- Why the web needs PFS more than ever (EFF.org)
Feel free to ask any questions in the comments, or add anything we missed. Thanks!